
Man gets four years in prison for $1.5M Apple Pay fraud | appleinsider
A good take away from AppleInsider's article is that Apple may own Apple Pay. But, it's the bank's responsibility to police and secure verification.
A U.S. district judge has sentenced a 30-year-old Miami resident to over four years in federal prison for his part in a criminal enterprise that leveraged Apple Pay to make more than $1.5 million in purchases using victims' credit cards. appleinsider

Android TV bug gave users access to strangers' Google Photos | Engedget
“On a good day, Android TV, Google's Android OS for TVs, allows users to display photos from their Google Photos albums as screensavers. That's a nice perk -- when it doesn't potentially share your private photos with strangers. Over the weekend, a disturbed Android TV owner took to Twitter when he realized, through the Google Home app, he could access a massive list of random accounts, as well as photos they'd added to their Google Photos albums.” Engadget
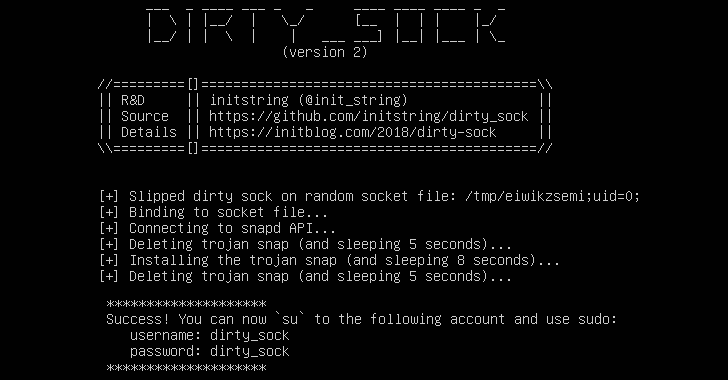
Snapd Flaw Lets Attackers Gain Root Access On Linux Systems | TheHackerNews
Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local attacker or a malicious program to obtain root privileges and total control over the targeted system.

NVIDIA GPUs weren't immune to Spectre security flaws either | Engadget
It's not just your processor and operating system that are affected by the Meltdown and Spectre memory vulnerabilities -- your graphics card is, too. To that end, NVIDIA has detailed how its GPUs are affected by the speculative execution attacks and has started releasing updated drivers that tackle the issue. All its GeForce, Quadro, NVS, Tesla and GRID chips appear to be safe from Meltdown (aka variant 3 of the attacks), but are definitely susceptible to at least one version of Spectre (variant 1) and "potentially affected" by the other (variant 2). The new software mitigates the first Spectre flaw, but NVIDIA is promising future mitigations as well as eventual updates to address the second.

Millions of Up-to-Date Apple Macs Remain Vulnerable to EFI Firmware Hacks | thehackernews
Researchers from security firm Duo Labs analysed over 73,000 Macs systems and discovered that a surprising number of Apple Mac computers either fails to install patches for EFI firmware vulnerabilities or doesn't receive any update at all.

Privacy Under Attack | Infographic by Untangle
Great infographic by Untangle highlighting net neutrality and changes in legislation.

Face ID anti-FUD: Why you shouldn't be worried about iPhone X unlock | iMore
An excellent article by Rene Ritchie of iMore, talking about unlocking the new iPhone X with Face ID and anti-FUD.
I must say I was nervous when TouchID first came out, and I'm getting that same fuzzy feeling again. I do hope they build in some 2nd factor authorization; it could be something as simple a checking to see if an Apple watch is on. But I've always planned for the worst while hoping for the best; it's just the way I'm wired.

Hackers Gain Direct Access to US Power Grid Controls | WIRED
Symantec on Wednesday revealed a new campaign of attacks by a group it is calling Dragonfly 2.0, which it says targeted dozens of energy companies in the spring and summer of this year. In more than 20 cases, Symantec says the hackers successfully gained access to the target companies’ networks

Hackers Can Silently Control Siri, Alexa & Other Voice Assistants Using Ultrasound | thehakersnews
A team of security researchers from China's Zhejiang University have discovered a clever way of activating your voice recognition systems without speaking a word by exploiting a security vulnerability that is apparently common across all major voice assistants.
Dubbed **DolphinAttack**, the attack technique works by feeding the AI assistants commands in ultrasonic frequencies, which are too high for humans to hear but are perfectly audible to the microphones on your smart devices.

WannaCry Ransomware Decryption Tool Released; Unlock Files Without Paying Ransom | thehackernews
If your PC has been infected by WannaCry – the ransomware that wreaked havoc across the world last Friday – you might be lucky to get your locked files back without paying the ransom of $300 to the cyber criminals.

Beware! Hackers Can Steal Your Windows Password Remotely Using Chrome - Thehakernews
A security researcher has discovered a serious vulnerability in the default configuration of the latest version of Google's Chrome running on any version of Microsoft's Windows operating system, including Windows 10, that could allow remote hackers to steal user's login credentials.

Vulnerability Disclosed in Ubquiti Networks Admin Interface | Threatpost
This command injection flaw exposes the Ubiquiti admin interface to a number of risky attacks, SEC Consult said. For example, an attacker could connect to a vulnerable device by opening a port binding or reverse shell, and also change the password because the service runs as root. “The vulnerability can be exploited by luring an attacked user to click on a crafted link or just surf on a malicious website,” SEC Consult said in its advisory. “The whole attack can be performed via a single GET-request and is very simple since there is no CSRF protection.”

Hackers Threaten to Remotely Wipe 300 Million iPhones Unless Apple Pays Ransom | The Hacker News
It has been found that a mischievous group of hackers claiming to have access to over 300 million iCloud accounts is threatening Apple to remotely wipe data from those millions of Apple devices unless Apple pays it $75,000 in crypto-currency or $100,000 worth of iTunes gift cards. The hacking group, who identified themselves as 'Turkish Crime Family,' has demanded a ransom to be paid in Bitcoin or Ethereum, another popular crypto-currency.

Unpatchable 'DoubleAgent' Attack Can Hijack All Windows Versions — Even Your Antivirus! | The Hacker News
A team of security researchers from Cybellum, an Israeli zero-day prevention firm, has discovered a new Windows vulnerability that could allow hackers to take full control of your computer. Dubbed DoubleAgent, the new injecting code technique works on all versions of Microsoft Windows operating systems, starting from Windows XP to the latest release of Windows 10. What's worse? DoubleAgent exploits a 15-years-old undocumented legitimate feature of Windows called "Application Verifier," which cannot be patched.

Amazon hands over Alexa data after murder suspect gives the okay | engadget
Amazon has agreed to hand over Alexa data to prosecutors in a murder trial after the defendant, an Echo owner, gave permission. The company had initially refused to do so, saying it "seeks to protect the privacy rights of its customers" and that Alexa's questions and answers are protected by the first amendment.

Trump signs executive order stripping non-citizens of privacy rights
Andrew Tarantola said it well in TechCrunch's artilce "Enforcing privacy policies that specifically "exclude persons who are not United States citizens or lawful permanent residents," while aimed at enhancing domestic immigration laws, effectively invalidates America's part of the Data Shield agreement, opens the current administration up to sanctions by the EU and could lead our allies across the Atlantic to suspend the agreement outright."

Over 27,000 MongoDB Databases Held For Ransom Within A Week | thehackernews
Are you running a MongoDB or know someone that is? It may be time to make sure it's patched and configured correctly. Last Monday a security researcher identified nearly 200 instances of MongoDB installations that have been erased and held for ransom, asking victims to pay hefty ransoms for the data to be restored. By Tuesday, this number reached approximately 2,000 databases and by Friday this count reached 10,500.

FTC sues D-Link for failure to secure webcams, routers from online attacks | appleinsider
A must read if you own a D-Link router or webcam as they are under fire from the Federal Trade Commission for not doing enough to secure its products, including connected home devices —a threat Apple has countered via secure authentication chips in HomeKit-certified hardware

Skype Backdoor Discovered | The Hacker News
The backdoor actually resides in the desktop Application Programming Interface (API) that allows third-party plugins and apps to communicate with Microsoft-owned Skype — the popular video chat and messaging service.

Apple iOS v10.1.1 - iCloud & Device Lock Activation Bypass via local Buffer Overflow Vulnerability - YouTube
There are claims by two anonymous researchers in which they found a way to bypass the activation lock feature in iOS. I have not personally tried this yet, but plan to and will report back at that time. However, it's important to know in the meantime.
Their attack focuses on buffer overload. One of the few things allowed from the activation lock screen is connecting to a Wi-Fi network. It's said that by crashing the service that enforces the lock screen by entering very long strings of characters in the WPA2-Enterprise username and password fields and in time freezing. He then proceeded to use an Apple smart cover to put the device to sleep and reopen after a few seconds later the Wifi screen crashes to the home screen bypassing the activation lock.

